Registry
By leveraging CAPI cluster lifecycle hooks, this handler deploys an OCI Distribution registry,
at the AfterControlPlaneInitialized phase and configures it as a mirror on the new cluster.
The registry will be deployed as a StatefulSet with a persistent volume claim for storage
and multiple replicas for high availability.
A sidecar container in each Pod running Regsync will periodically sync the OCI artifacts across all replicas.
Deployment of this registry is opt-in via the provider-specific cluster configuration.
The hook will use the Cluster API Add-on Provider for Helm to deploy the registry resources.
Example
To enable deployment of the registry on a cluster, specify the following values:
apiVersion: cluster.x-k8s.io/v1beta1
kind: Cluster
metadata:
name: <NAME>
spec:
topology:
variables:
- name: clusterConfig
value:
addons:
registry: {}
Registry in the workload cluster
When the registry is enabled in the management cluster, it can also be automatically enabled in the workload cluster. To enable this behavior, set the following feature gate on the controller:
--feature-gates=AutoEnableWorkloadClusterRegistry=true
It is also possible to disable this behavior by setting the following annotation on the Cluster resource:
annotations:
caren.nutanix.com/skip-auto-enabling-workload-cluster-registry: "true"
All images pushed to the management cluster's registry can be automatically synced to the workload cluster's registry. To enable this behavior, set the following feature gate on the controller:
--feature-gates=SynchronizeWorkloadClusterRegistry=true
It is also possible to disable this behavior by setting the following annotation on the Cluster resource:
annotations:
caren.nutanix.com/skip-synchronizing-workload-cluster-registry: "true"
Registry Certificate
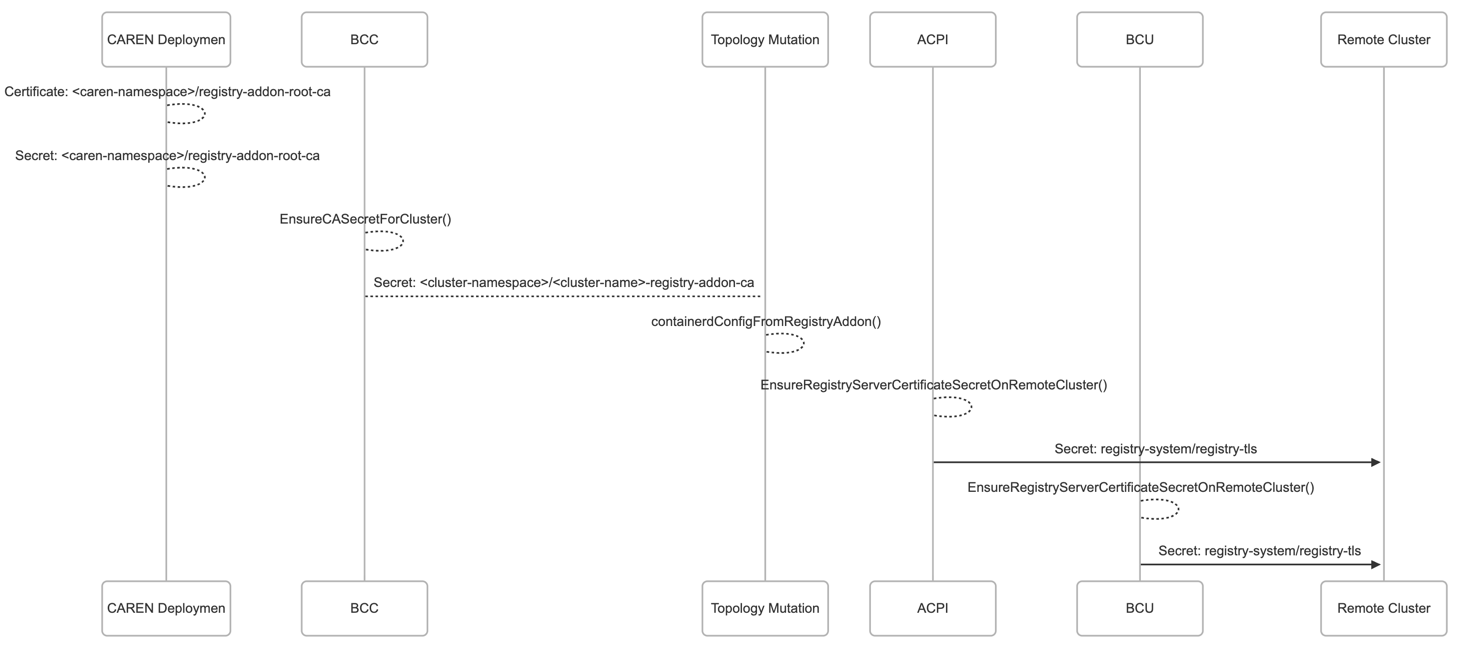
- A root CA Certificate is deployed in the provider's namespace.
- cert-manager generates a 10-year self-signed root Certificate
and creates a Secret
registry-addon-root-cain the provider's namespace. - BCC handler copies
ca.crtfrom theregistry-addon-root-caSecret to a new cluster Secret<cluster-name>-registry-addon-ca. A client pushing to the registry can use either the root CA Secret or the cluster Secret to trust the registry. - The cluster CA Secret contents (
ca.crt) is written out as files on the Nodes and used by Containerd to trust the registry addon. - During the initial cluster creation, the ACPI handler uses the root CA to create a new 2-year server certificate
for the registry and creates a Secret
registry-tlson the remote cluster. - During cluster upgrades, the BCU handler renews the server certificate
and updates the Secret
registry-tlson the remote cluster with the new certificate. It is expected that clusters will be upgraded at least once every 2 years to avoid certificate expiration.
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.